| << Chapter < Page | Chapter >> Page > |
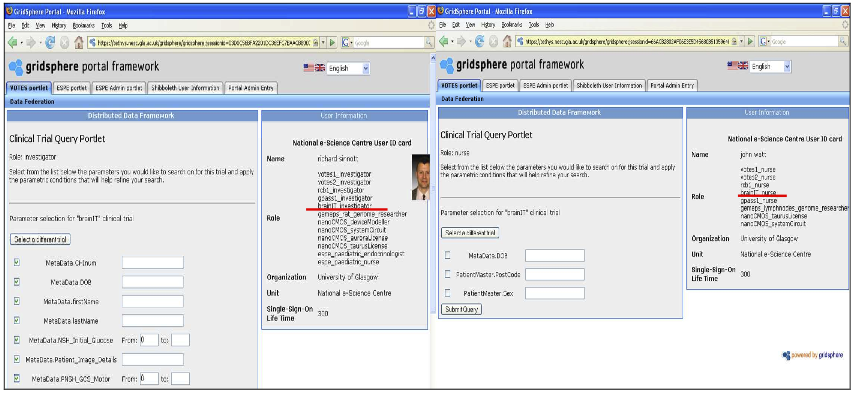
A Content Configuration Portal (CCP) was developed to allow the dynamic configuration of contents of a portal based upon presented user privileges that are presented from Shibboleth. Intuitively, CCP allows users to access and use client portlets that are associated with their given privilege sets as defined by a portal administrator. An example of application of the CCP in the neurological domain is shown in Figure 2 where the portlet on the right is for researchers with a brainIT-investigator role and the portlet on the left for researchers with a brainIT-nurse role. The definition of these roles and their association with specific portlets (giving access to remote services/data), and finally their dynamic configuration through information presented by Shibboleth is at the heart of the CCP.
The SPAM-GP Attribute Certificate Portlet (ACP) is a JSR-168 compliant portlet that supports sites wishing to define and enforce their own remote authorization. Thus it is unlikely that a resource provider will simply delegate their security and access control to a potentially remotely managed portal. ACP allows the security information (attributes) to be signed and stored in a local attribute store for use by remote providers in enforcing their own local authorization policies. Currently the ACP has been applied successfully to a range of distributed resources and resource providers including those in the clinical domain through projects such as the Medical Research Council (MRC) funded Virtual Organisations for Trials and Epidemiological Studies project (VOTES), the social science domain through projects such as the Economic and Social Science Research Council (ESRC) funded Data Management through e-Social Science project (DAMES) and the geospatial domain through projects such as the Joint Information Systems Committee (JISC) funded Secure Access to Geospatial Services project (SeeGEO).
Employment of an adequate trust and security model is crucial to e-Research. It must provide researchers with easy access to shared heterogeneous, distributed resources while ensuring adequate protection of those resources. Some disciplines place more emphasis on security, for instance the medical field where patient confidentiality is paramount, but all disciplines undertaking e-Research involving distributed systems require a model that takes into account issues of single sign-on authentication and authorisation which should apply to all computational and data resources. In this chapter, we have presented examples of models that work well to address these issues of resource sharing. These models are now being used in a variety of diverse large scale projects including major European clinical trials; nanoCMOS electronics; social sciences and the arts and humanities amongst others. More information on these solutions and the work of NeSC at Glasgow is available at www.nesc.ac.uk/hub .
This work was funded by a variety of grants from the EPSRC, ESRC, JISC and the MRC. We gratefully acknowledge their support. More information on NeSC at Glasgow and the security-oriented projects that they are involved in is available at www.nesc.gla.ac.uk/projects .
Watt, J., Sinnott, R.O., Ajayi, O., Jiang, J. and Koetsier, J. (2006). A Shibboleth-Protected Privilege Management Infrastructure for e-Science Education . 6th IEEE International Symposium on Cluster Computing and the Grid , CCGrid2006, May, Singapore.
Sinnott, R.O., Watt, J., Chadwick, D.W., Koetsier, J., Otenko, O., and Nguyen, T.A. (2006). Supporting Decentralized, Security focused Dynamic Virtual Organizations across the Grid . 2nd IEEE International Conference on e-Science and Grid Computing , Amsterdam, December.
Sinnott, R.O., Watt, J., Ajayi, O. and Jiang, J. (2006). Shibboleth-based Access to and Usage of Grid Resources . IEEE International Conference on Grid Computing , Barcelona, Spain, September.
Sinnott, R.O. (2008). Grid Security. In Wang, L, Jie, W. and Chen, J. (eds.) Grid Computing: Technology, Service and Application , CRC Press, May.
Sinnott, R.O., Chadwick, D., Doherty, T., Martin, D., Stell, A., Stewart, G., Su, L. and Watt, J. (2008). Advanced Security for Virtual Organizations: Exploring the Pros and Cons of Centralized vs Decentralized Security Models . 8th IEEE International Symposium on Cluster Computing and the Grid (CCGrid 2008), May, Lyon, France.
Wei, J., Arshad, J. and Sinnott, R.O. (2010). A Review of Grid Authentication and Authorization Technologies and Support for Federated Access Control, to appear in ACM Computing Surveys, January.

Notification Switch
Would you like to follow the 'Research in a connected world' conversation and receive update notifications?